This new procedure succeeds the GridKa CA and is in production! Requests to GridKa will be denied. It also holds for renewals of GridKa certs! For support please contact grid_AT_desy.de.
Note: After 1 year you will be notified of the expiration of your current certificate. Obtain a new one with the same procedure as before. As the DN does not change (check!) VOMS and DIRAC are not affected.
News
2023-10-25
2023-10-25: Grid Certificates available again
The issue at the Sectigo IGTF CA was resolved by Sectigo and it is possible again to request Grid User Certificates.
Unfortunately, the issuer CA DN was changed, meaning that new user certificates differ in a detail from previous certificates. Due to limitations at KEK with the Belle VO, existing VOMS user accounts cannot be adapted. Thus, when requesting a new user certificate, this certificate has to be registered as a new user account at a VO - meaning that after obtaining a new certificate the registration procedure at a VO has to be done again with this new certificate.
The documentation in the following has been updated
Introduction
On order to access global Grid resources, users must hold a valid personal Grid user certificate (authentication) AND users must be member of a Virtual Organization (VO) (authorization).
A valid Grid user certificate is a prerequisite to request membership in a VO. Users usually have one Grid user certificate. Multiple VO membership is possible. A Grid user certificate can be seen as an analogy to a passport, whereas the VO membership compares to a visa.
The personal Grid user certificate is issued by a Certification Authority (CA). When certificates are requested the CA requires an authorization by the institution of the user against an Identity Provider (IdP).
A Grid user certificate (format X509) consists of a private key with a private password and a certified public key. The private key and the password is exclusively possessed by the user and is NOT known to the Registration Authority (RA) or Certification Authority (CA) at any stage.
A certificate is valid for one (1) year. As long as the same CA is used it can be renewed without changing the identity (DN). Users get notified by the GÉANT TCS via email 30 days before the expiration date. It is strongly recommended to renew the certificate before its expiration.
The certificate can/should be copied to all devices/browsers which need it.
Glossary
- AAI: Authentication and Authorization Infrastructure
- CA: Certification authority (issues certificates)
- DN: Distinguished Name (identity of the user)
- IAM: Identity and Access Management System
- IdP: Identity Provider (service of an institution which knows its users)
- IGTF: The International Grid Trust Federation (collection of known CAs)
- OSG: Open Science Grid (the US Grid infrastructure)
- SSO: Single Sign-On (unique user account at the institution)
- VO: Virtual Organization (the collabration in the Grid)
- VOMS: Virtual Organization management Service (a services to manage the VO members)
- WLCG: Worldwide LHC Computing Grid (the HEP Grid infrastructure)
Authorities
DESY users may obtain personal Grid user certificates from the GÉANT TCS CA. It is part of The International Grid Trust Federation (IGTF) hence certificates are accepted by all Grid sites in WLCG and OSG.
DESY / (UHH) employees may use their account to authenticate against GÉANT via the DESY AAI. Use the portal Certificate Manager SSO Check to test your account against the Identity Provider (IdP). A DESY email address is required to be associated with the account!
Non-DESY users can NOT use the portal and should check with their home institution officials how to proceed. The DFN Verein in Germany operates a CA. For the members of LHC experiments the CERN CA might be a good choice. Please also check EUGridPMA.
User holding a CERN account might use the CERN CA!
Links
Procedure
- Test your credentials (account_name / password) in Certificate Manager SSO Check against an Identity Provider (IdP). Select your home institution ('DESY' or '(UHH)').
- if you encounter problems, please screenshot your status information in the SSO check portal for further debugging.
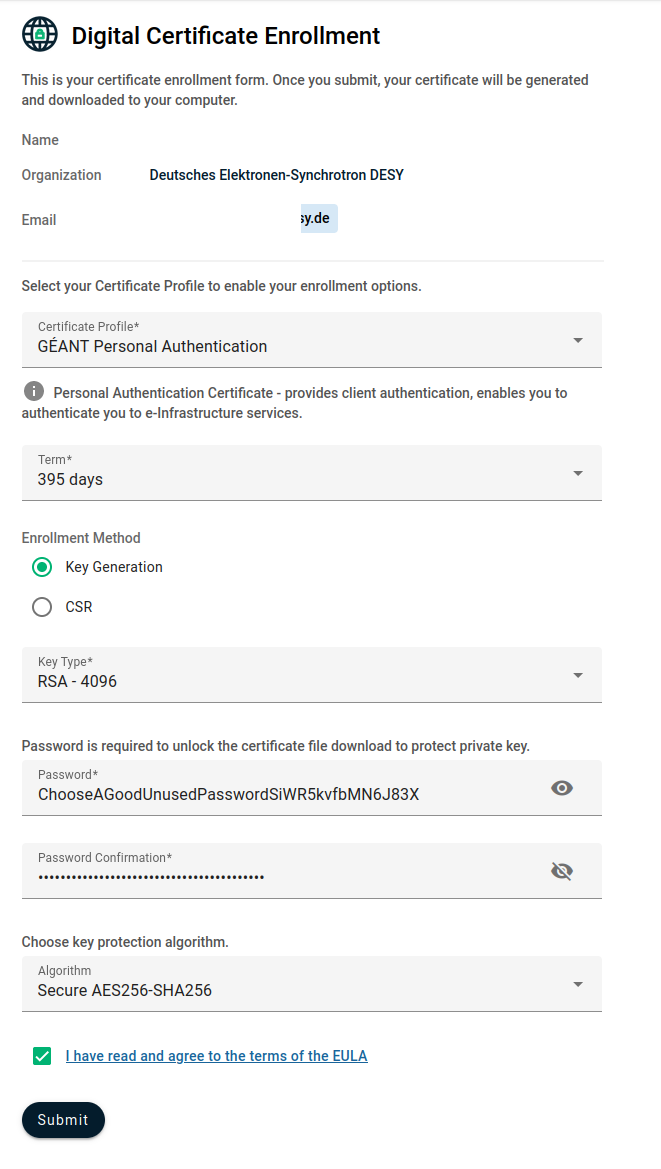
- Request a Grid user certificate in GEANT TCS User Cert (attention: do not select the
GEANT Personalemail signing and encryptionorGÉANT Personal Automated Authenticationoptions but only GÉANT Personal Authentication) - profile: GÉANT Personal Authentication
- choose button: Key Generation (not CSR)
algorithm: RSA-4096
- Password: Choose a password with sufficient entropy (>16 random characters or alternatively >6 random words with each at least 5 characters), that has not been used anywhere else. The password cannot be recovered, if it gets lost or forgotten.
key protection algorithm: Secure (AES256-SHA256)
Example
- After a short while the new cert can be downloaded from the page
On Linux machines with Grid setups, the certificate and key files are usually placed in the directory
~/.globus/- Download certificate file and copy it to ~/.globus/usercert.p12
- if you use the default approach, the downloaded p12 file will contain both, the certificate and the key
- the certificate is your passport, you "show" to services to authenticate yourself
- if you have generated the key file separately and copy as well the key file to ~/.globus/userkey.p12
- the key file is your secret key, that unlocks your certificate. Protect the key with a good password, do not share the key with anyone and backup the key, as it cannot be recovered, if the file got lost or you forgot the password
- optional: for usage in the Grid, you will have to convert the certificate+key from its "
p12" file format into two "pem" formatted files: one file "usercert.pem"containing just the certificate and one file"userkey.pem", containing the password secured key. See 'Technicalities' below how to do it withopenssl.
- Download certificate file and copy it to ~/.globus/usercert.p12
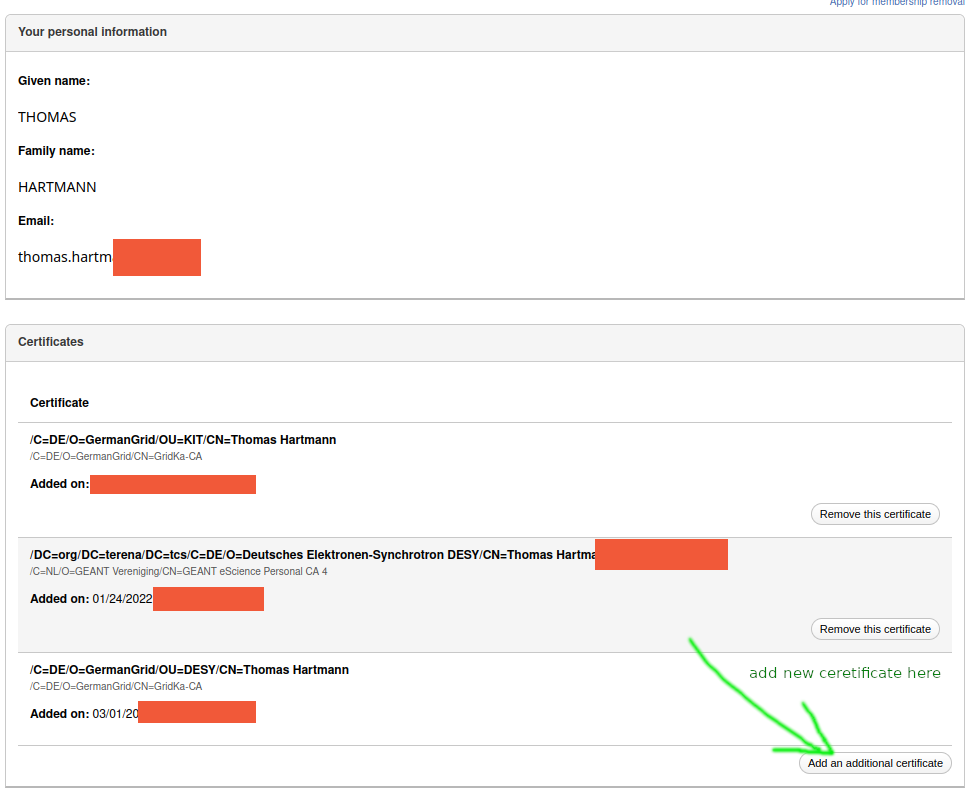
- Your user certificate (passport) has to be registered at your experiment VO (VOMS) if the DN has changed. See links at the bottom.
- If you have never registered before, go for it now.
- As long as the same CA is used renewed certificate has the same DN. No action is needed if you had registered the DN already. Better check the DN though!
- A new certificate from a new CA contains a new DN:
- Either add the new DN using your still valid already registered (old) certificate.
- Or contact VO/VOMS admin to add the new DN to your VOMS record
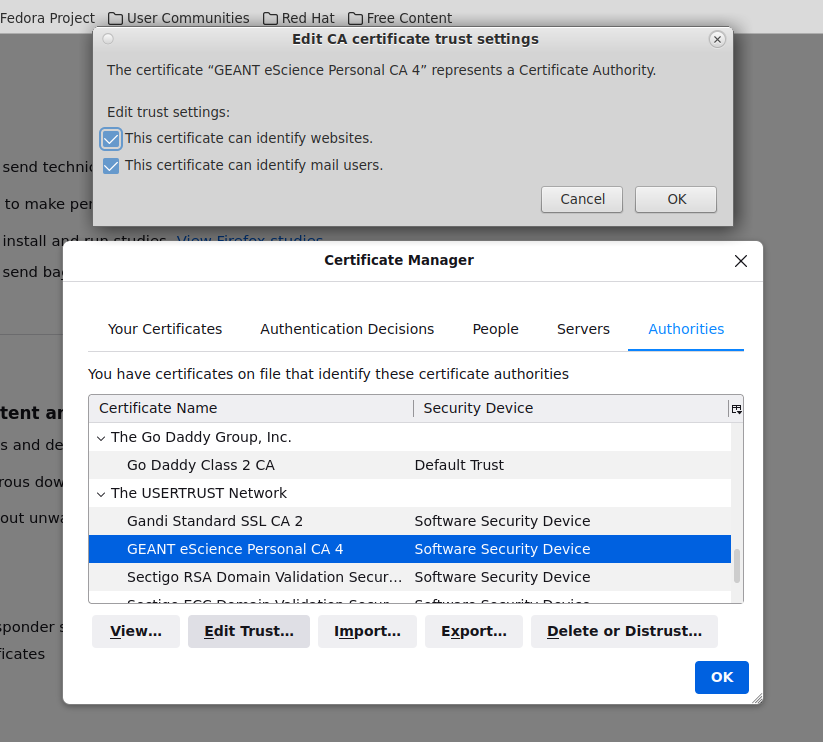
Depending on your browser version, it might be necessary to check in your browser's certificate trust settings → the `
The USERTRUST Network` certificate authority needs to be trusted for all operationsFirefox:
Settings → Privacy & Security → Certificates → View Certificates → Authorities
in the `The USERTRUST Network` block, select `Edit Trust` if for `GEANT eScience Personal CA` and ensure, that all trust settings are enabled
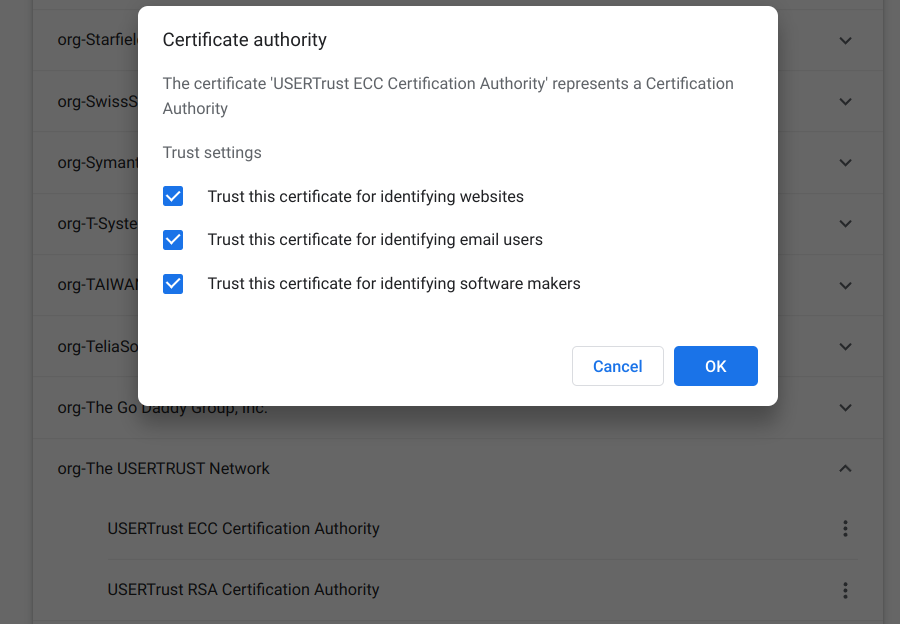
- Chrome
Settings → Security → Manage Certificates → Authorities
search for `org-The USERTRUST Network` and ensure, that for both entries under `⋮` →Editall trust settings are selected
To avoid problems with previous certificates, restart your browser after importing and backing up the certificate and key has been done. Always delete expired certificates!
I.e., to quit Firefox or Chrome explicitly select `Quit` or `Exit`, respectively, from the browsers' menus.- if everything works with your new certificate, you should delete your previous certificate
- You can print a summary of your grid user certificate running the script
/cvmfs/grid.desy.de/usr/local/bin/my-grid-cert
Select your institution according to your affiliation. As of Mar 2022 we have seen successful request for:
- Deutsches Elektronen-Synchrotron DESY (desy.de)
- Universität Hamburg (UHH) (uni-hamburg.de)
Check your the settings of your preferred email address if
pal52: [~] ldapsearch -H ldap://it-ldap-slave:1389 -x -LLL -b 'ou=people,ou=rgy,o=desy,c=de' "(cn=first last)" mail
As the DN of your certificate might change, hence you might have to register the new DN with VOMS (and DIRAC etc.). This is most easy as long as your old/other certificate is still valid.
Browser Plugins and Extensions
If you encounter problems, please check if you have browser plugins or extensions enabled, that could interfere with the login and certificate & key generation.
For example, Chrome's automatic translation of web pages (German ↔ English) might result in unexpected behavior.
It is recommended to use a plain firefox.
Renewal
After one year Grid user certificates expire and must be renewed. Users will be notified by email 30 days in advance of the expiration. A renewal is technically a new request. Simply follow the Procedure above. As the DN does not change (check!) no action to VOMS or DIRAC is needed.
Cert lifetime
naf-XXX: [~] source /cvmfs/grid.desy.de/etc/profile.d/grid-ui-env.sh naf-XXX: [~] grid-cert-info -subject -enddate
Technicalities
Technically a new private/public key pair is created with every renewal while the DN stays the same!
Finding certificates in Firefox browser
Preferences -> Privacy & Security -> Certificates -> View Certificates -> Your Certificates (-> Backup)
Download/export the file either form the browser or directly to the ~/.globus/usercert.p12 directory and make sure to safe the old files. Then use openssl to extract ~/.globus/usercert.pem and ~/.globus/userkey.pem. Have your export passphrase at hand!
### move into your .globus directory in your home directory ### > cd ~/.globus ### rename the previous certificate and key files ### > mv usercert.p12 usercert.p12.old > mv usercert.pem usercert.pem.old > mv userkey.pem userkey.pem.old > ls -l -r-------- 1 account group 8213 24. Jan 14:36 usercert.p12 -r-------- 1 account group 2611 31. Jan 13:40 usercert.p12.old ### extract your user certificate from the p12 file, you will need to enter your export passphrase. ### > openssl pkcs12 -clcerts -nokeys -in usercert.p12 -out usercert.pem ### extract your secret private key from the p12 file. First, you will need your export passphrase to open the p12. Secondly, you will need to enter a password to secure the key file - this passowrd will be necessary in the future to use your user key. ### > openssl pkcs12 -nocerts -in usercert.p12 -out userkey.pem > ls -l -r-------- 1 account group 8213 24. Jan 14:36 usercert.p12 -r-------- 1 account group 8213 24. Jan 14:38 usercert.pem -r-------- 1 account group 2611 31. Jan 13:42 userkey.pem
Importing certificates into Firefox browser
Preferences -> Privacy & Security -> Certificates -> View Certificates -> Your Certificates (-> Import)
Lost private/public keys or the password can NOT be recovered by any means by the CA or RA.
Please back up certificates and keys in a safe manner.
It is the 'usercert.p12' which you distribute to your browsers of choice even on other hosts.
The two extracted '~/.globus/user*.pem' files must be present on all hosts you use Grid commands on!
Keep the key file userkey.pem save - it is the key to unlock your usercert.pem certificate. Do not share the key file with anyone and secure it with a good password!
Known Issues
- Make sure to export the certificate from the browser you requested and retrieved it with in as 'usercert.p12'.
- Make sure you remember the pass-phrase for the key and for the export.
- Make sure your have 'usercert.pem' and 'userkey.pem' in the direcory ~/.globus/
- Make sure the access permissions to 'usercert.pem' and 'userkey.pem' are correct.
- We found that a cert did now work with 'voms-proxy-init' although everything had been checked. Only a new extraction from the exported cert 'usercert.p12' helped.
Inspecting Grid user certificates
Please make sure your public (usercert.pem) and private (userkey.pem) keys are:
- in the correct directory,
- have the correct permissions,
- show your DN,
- are valid,
- match each other (have the same md5sum),
- your remember the password.
> cd ~/.globus > ls -l ... -r--r--r-- 1 account group 1728 8. Apr 09:36 usercert.pem -r-------- 1 account group 2012 8. Apr 09:36 userkey.pem > openssl x509 -subject -issuer -dates -noout -in usercert.pem subject= /DC=org/DC=terena/DC=tcs/C=DE/O=Deutsches Elektronen-Synchrotron DESY/CN=Andreas Gellrich gellrich_AT_desy.de issuer= /C=NL/O=GEANT Vereniging/CN=GEANT eScience Personal CA 4 notBefore=Jan 24 00:00:00 2022 GMT notAfter=Jan 24 23:59:59 2023 GMT > openssl x509 -noout -modulus -in usercert.pem | openssl md5 > openssl rsa -noout -modulus -in userkey.pem | openssl md5
VO Specifics
List of VOMS Servers
The obsolete documentation for the previous Grid user certificates from GridKa CA can be found under [ Grid User Certificates Old ]- intended just for historic reference.